RELATED ARTICLES
SHARE ARTICLE
5 Open Source SIEM Tools
Learning Objectives
• Discover SIEM solutions
• Learn what a SIEM does
• Identify features of a SIEM

The last decade has shown organizations that disregarding cybersecurity can lead to massive data breaches that cost millions in reparations, legal fees, and containment efforts. Whether you run a small or large enterprise business, cyber-threats are a real concern that must be addressed in the most efficient way possible.
Cybersecurity is necessary, but it’s also a complicated and misunderstood area of IT for many businesses. An entire cybersecurity team of analysts is an expensive hire, so companies turn to Security Information and Event Management (SIEM) systems to mitigate risk and detect cyber-threats. The next challenge is to find the right SIEM that fits your budget, infrastructure, and IT preferences. We’ve collected a list of five SIEM applications to help you find the right one.

What Does an Open Source SIEM Do?
Knowing that you need a SIEM is the first step, but you also need to understand what a SIEM does and what factors make a good management application. Every SIEM has its advantages and disadvantages, but the overall goal of a good SIEM is to collect data from network resources and endpoints and analyze events to detect threats and alert administrators.
SIEM applications are primarily used by large enterprise organizations, but several open-source and affordable options are available to smaller businesses. Your goals should be to find a SIEM that suits your needs, but it should also be effective at detecting suspicious traffic patterns. Here are a few features that should be included in your SIEM solution:
Identifies Threat Responses
- Analyzes network resources, endpoint, and user behavior patterns
- Low false positives that reduce analyst fatigue
- Tracks lateral movements from suspicious users (e.g., a change of IP address or credentials)
- Alerts administrators after anomaly thresholds are met
- Prioritization of threats and containment strategies
Provides a Holistic Picture
- Collects data from several sources both on-premise and in the cloud
- Provides dashboards and reports for visualization of metrics and analytics
Meets Business Needs
- Costs per ingested data volume should be clear, with any additional costs clearly detailed
- Easily customized with business requirements and configurations

AlienVault OSSIM
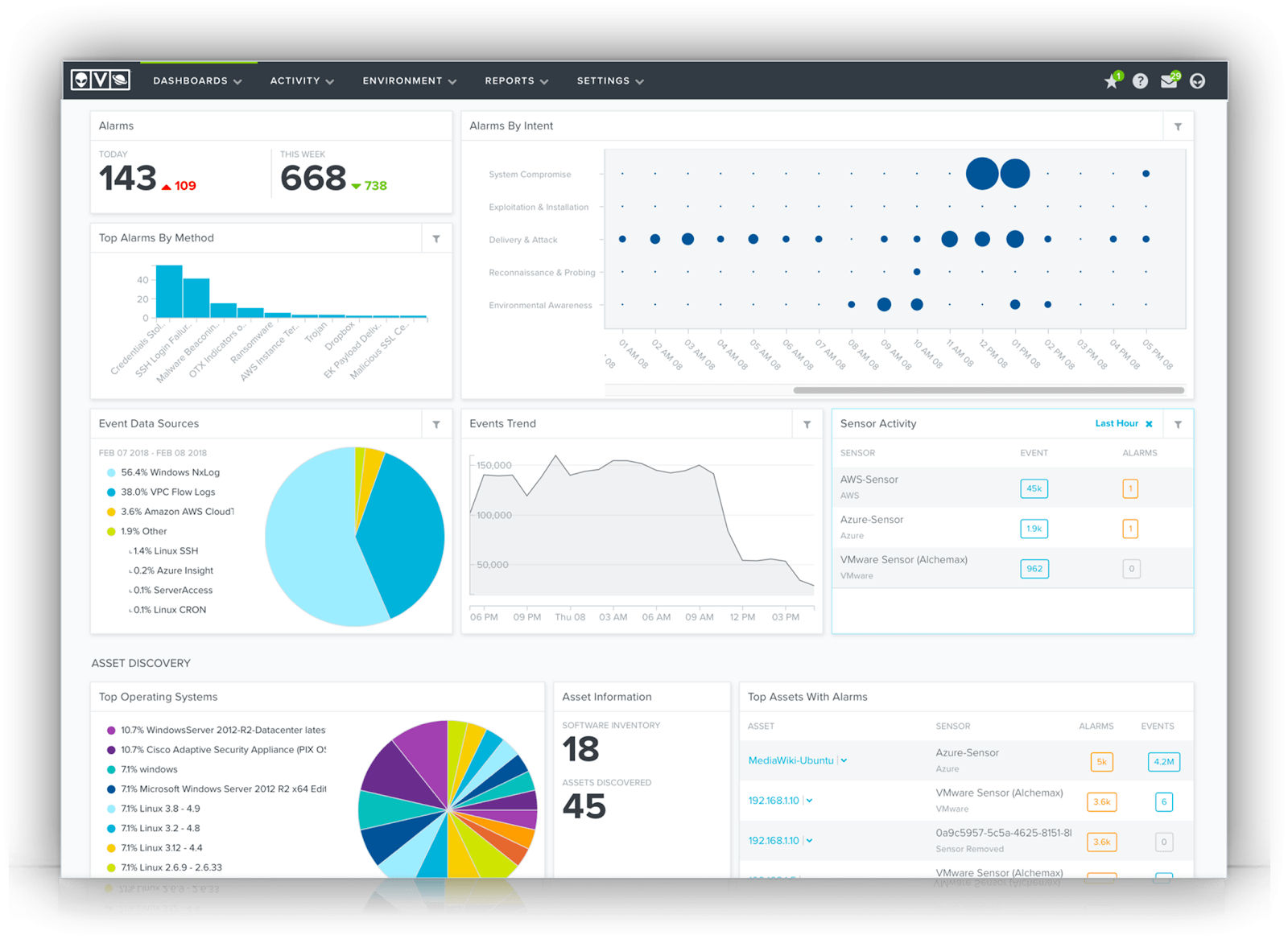
OSSIM is the open-source version of AlienVault, which has fewer features than the full enterprise USM version, but it’s still a useful tool for organizations with limited budgets and a need for a SIEM solution. For small businesses, the open-source version can be used on a single server. Still, administrators can upgrade to the USM version to scale to additional servers and resources when needed. The free version also does not have log management or cloud infrastructure monitoring capabilities.
The OSSIM (Open Source Security Information Management) in AlienVault OSSIM is a cybersecurity framework comprising Snort, Nagios, OSSEC, and OpenVAS. You can use the agent included with AlienVault to send logs to an endpoint for ingestion or install plugins to send events to third-party providers such as Cloudflare. It’s worth noting that AT&T bought OSSIM in 2019, so it’s now named AT&T Cybersecurity.

MozDef (Mozilla Defense Platform)

Mozilla is the developer responsible for the Firefox browser, so they’ve contributed a lot to the open-source community. MozDef is the cybersecurity side of their development efforts created to be scalable and fast. It works well with microservices as the system itself runs in Docker containers. Alerts use Elasticsearch indexing, but developers familiar with Python can use it to customize alert preferences.
Like the OSSIM framework, MozDef is also built on a set of third-party tools such as Elasticsearch for indexing, Meteor for the frontend UI, and Kibana for charts and graphics. According to Mozilla’s documentation, this SIEM can handle over 300 million events per day.

Wazuh

The foundation for Wazuh is an open-source SIEM named OSSEC. It started as a simple application with few features targeting small businesses, but it soon became a popular enterprise solution used to ingest syslog data or agent-based event collection. It’s built on Elastic Stack, which itself comprises Elasticsearch, Logstash, and Kibana.
Wazuh is a forked version of OSSEC, so it has several of the same features. It supports many of the orchestration tools common in a containerized environment, including Docker, Puppet, Chef, and Ansible. Unlike some of the other SIEM applications, it supports cloud infrastructure monitoring on AWS and Azure.
An interesting feature included with Wazuh is its compliance ruleset. For example, administrators can configure Wazuh to follow PCI-DSS v3.1 compliance. It also integrates with Splunk to provide visualization information within its dashboards.

Prelude OSS

Similar to AlienVault, Prelude OSS is the open-source version of the developer’s enterprise SIEM. It’s a great option for small businesses that need a SIEM but are testing various solutions or need an affordable alternative. Prelude OSS advantage is that it supports several log formats and integrates with other tools such as OSSEC, Snort, and Suricata. Prelude OSS uses the IDMEF format, so its data can be used with intrusion detection systems.
Because Prelude OSS is meant for small deployments, it has fewer features than the enterprise SIEMS and performance is limited. For businesses that need to evaluate SIEMs before purchasing an enterprise version, Prelude OSS is a good choice.

Sagan

Of the five SIEM solutions listed in this post, Sagan is the application with the best performance. Its main benefit is compatibility with Snort, an open-source intrusion prevention system (IPS). Together with Snort, Sagan can be used to detect and stop cyber-threats. Sagan detects the threat and Snort can be used to prevent threat damage. It’s perfect for businesses that use Snort or plan to implement an IPS in addition to a SIEM. Sagan was designed to be lightweight, so it’s also beneficial for companies that don’t need several features and want to focus on their application’s performance.

Conclusion
Every SIEM has its own features and advantages. It’s up to you to test the ones that can be configured with settings that meet your specific requirements. The right SIEM doesn’t have to be expensive to be effective, and many of the open-source solutions have several features that fit small and large businesses.






.svg)




